OSS vulnerabilities
The OSS Vulnerabilities tab of the application details section lets you see a complete list of findings introduced to your application using OSS libraries and packages.
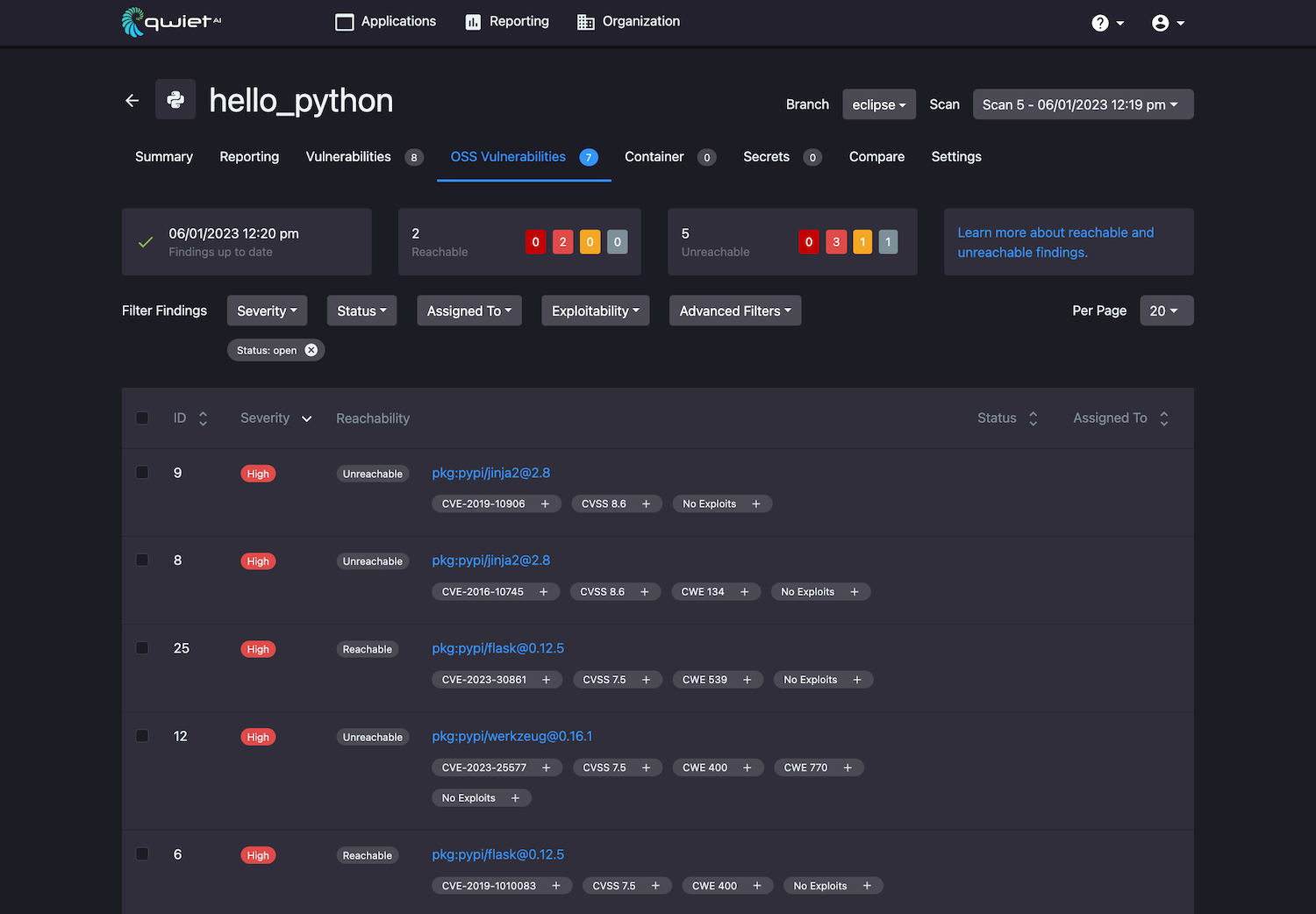
Summary information
At the top of the page is a row of summary information. This includes:
- Whether or not there are new results available. Qwiet continually checks your application and alerts you if there are new OSS vulnerabilities affecting your application discovered after you scanned your application (the timestamp displayed tells you the last time you submitted your app for analysis). If there are new findings, you should rescan your application to populate the results to the dashboard;
- The number of reachable findings, as well as the number of reachable findings for each severity level;
- The number of unreachable findings and the number of unreachable findings for each severity level.
For each finding in the complete list, you'll see its:
- ID
- Severity level (e.g.,
critical) - Reachability state
- Brief description, including vulnerability type and where it is found
- Tags (e.g.,
OWASP a1-injectionorCVSS 9) - Status (e.g.,
Fixed) - Assigned to information (i.e., the team member tasked with further work on this issue)
Filtering findings
You can filter the findings displayed by:
- Its severity level
- Its status
- The person the finding is assigned to
- Its exploitability status (e.g., display only findings that have known exploits or only findings that have no known exploits)
There is also a variety of Advanced Filters that you can use (e.g., CVSS score, EPSS score, reachability, CVE, CWE category, etc.).
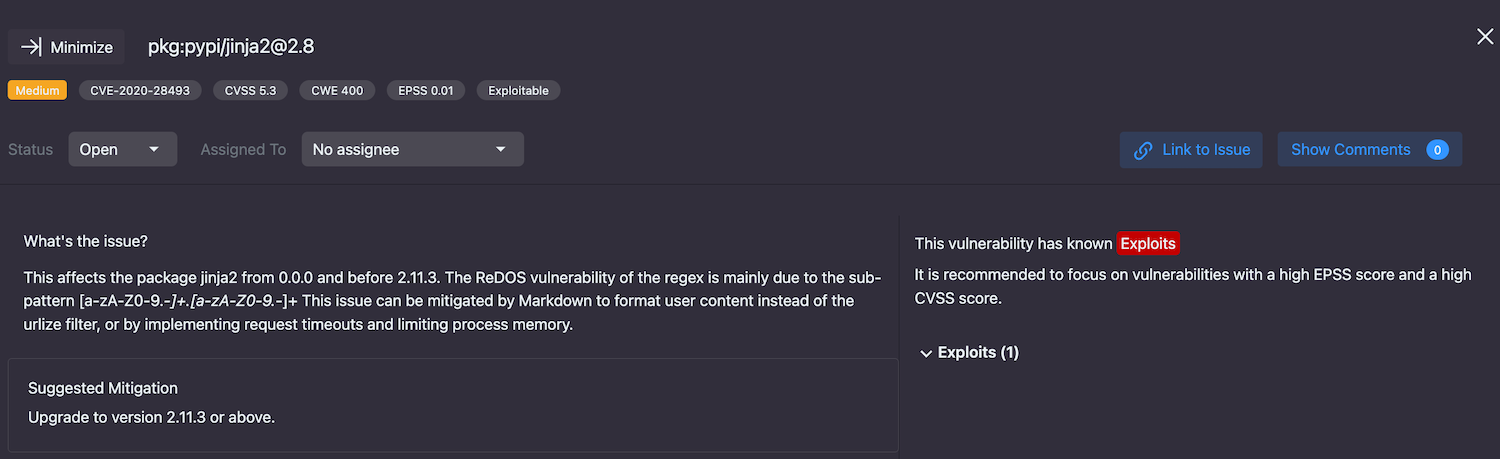
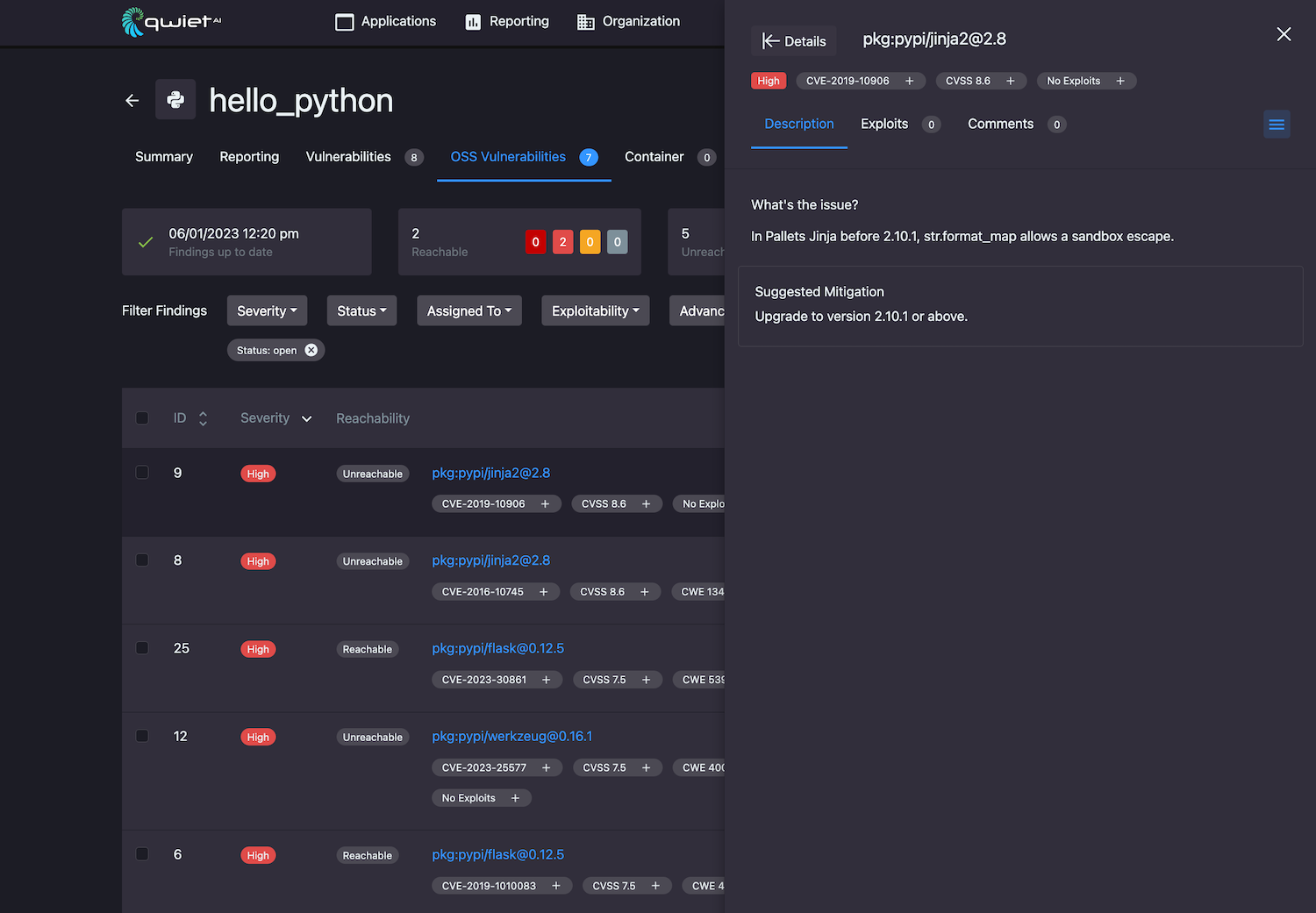
Viewing detailed finding information
Clicking on a finding in your results list will open a new window pane on the right with detailed information.
-
Description: the description tab features an in-depth write-up of what the issue is and why it is a problem, as well as mitigation suggestions for securing your app
-
Comments: the comments tab allows you and your team members to make notes specifically about this finding; if there are multiple comments, Qwiet displays them in reverse chronological order.
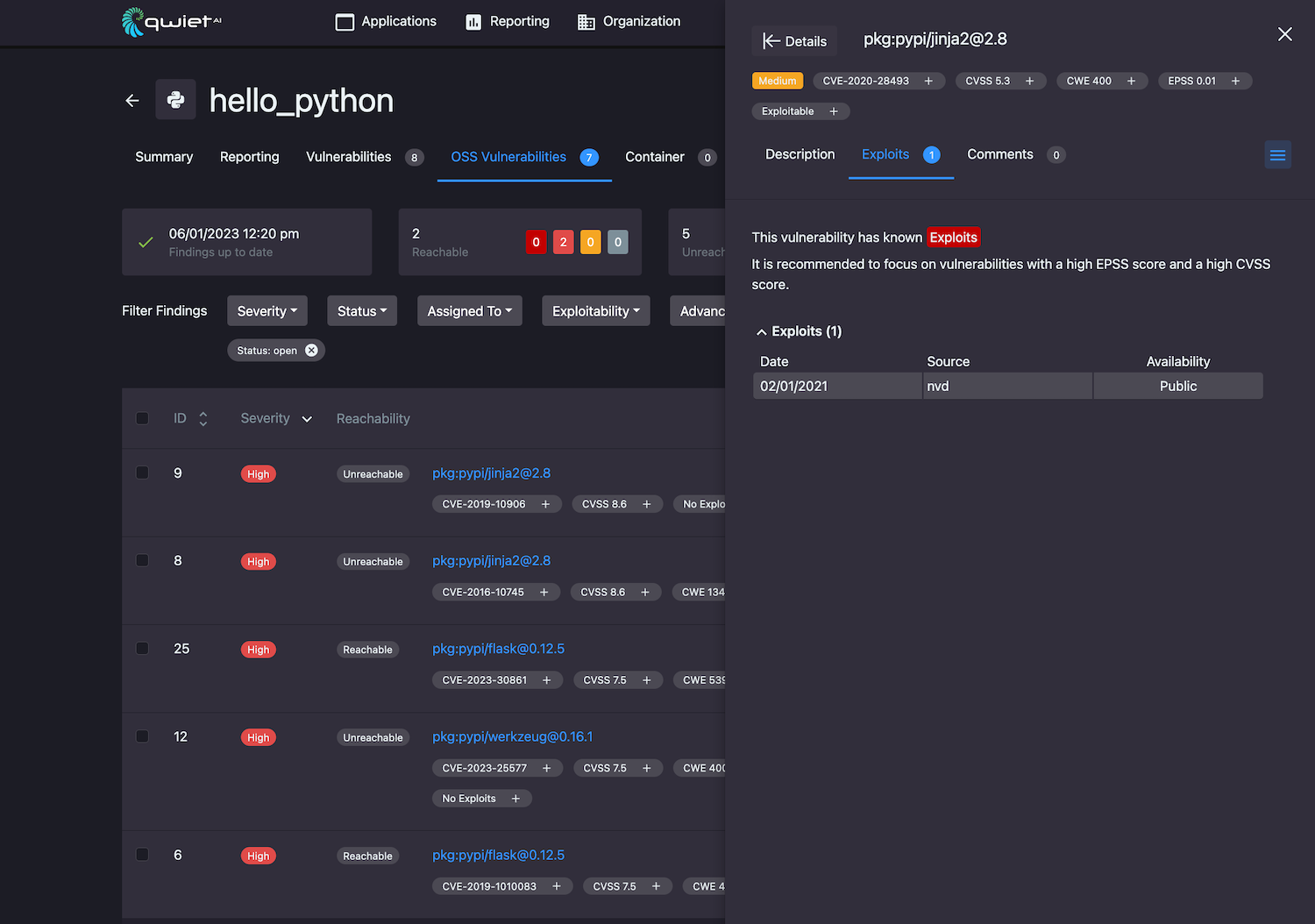
Exploits (Blacklight)
The Exploits section includes up-to-date exploitability information on the vulnerability, including the:
- Date reported
- The source providing a proof of concept of the exploit
- The availability of the exploit (e.g., public, private, or commercial)
The Exploit Prediction Score System (EPSS) score shown for the vulnerability can help you determine the severity and priority of a given vulnerability. The EPSS score falls between 0 and 1, and we recommend focusing on findings with a high EPSS score and high CVSS score.
Expanded details
In addition to the summary-level information displayed in the findings pop-up, you can open a larger window with additional features; to do so, click Details in the top-left of the initial window opened by Qwiet when you click on a specific finding.
The expanded details view features everything in the summary-level view, plus the ability to:
-
Set the finding status to reflect work that's been done (e.g., set the finding status to Fixed if you've mitigated the issue):
- Open: The default status value for a finding
- Fixed: Mark the finding as fixed if you've applied remediation of some type (note that setting this status does not fix the finding) so that Qwiet doesn't include the finding in the scan results
- Ignored: Mark the finding as ignored so it doesn't reappear in scan results. Used to indicate that something is a false positive or is unlikely to impact the application's security. If you set the status to ignored, you must also provide a comment that includes information on your reasoning for choosing this status
- 3rd Party: Mark the finding as 3rd Party to indicate that the finding is in a third-party library; you can't fix the finding at the moment, but you should return to it at a later date
To hide/show findings in the dashboard based on their statuses, use the Status filter (e.g., to display open and fixed findings while excluding those that are ignored or 3rd party, select the status filter's Open and Fixed values). To show all values, ensure no status filter values are selected.
Note that you can change the status at a later date if needed.
-
Assign to a team member the vulnerability for further research and work
-
Get a link to issue that's specific to this finding that you can share with others
Click Minimize in the top-left to return to the summary view.