Secrets v2
Qwiet uses Yelp's detect-secrets to deliver this feature. detect-secrets is licensed under the Apache License 2.0
When analyzing your code with preZero, your results will include secrets, or hard-coded values (e.g., client secrets, username/password combinations) and sensitive information (e.g., phone numbers and addresses), and any other vulnerabilities identified.
Before proceeding, please ensure that you have set up and authenticated with Qwiet. Then, analyze your application to obtain information about any secrets present in your application.
Scanning for secrets
Secrets scanning can be turned on for all applications on the Organization Settings page, or for each application on the Application Settings page. The setting is called Client-Side Secrets.
By default, Qwiet preZero looks for secrets present in checked-in files in the source repository of the project. Any data added during the build process will not be scanned.
In particular, files containing secrets that get added to Java's JAR/WAR/EAR files will only be considered as long as they're checked into the repository and contain the secrets prior to the build process starting. Any sort of interpolation of build time variables into resource files is not supported with secrets scanning.
Settings
Environment variables take precedence over Application Settings, and Application Settings take precedence over Organization Settings. If a particular setting is not set at the application level, the value from the Organization Settings will be used
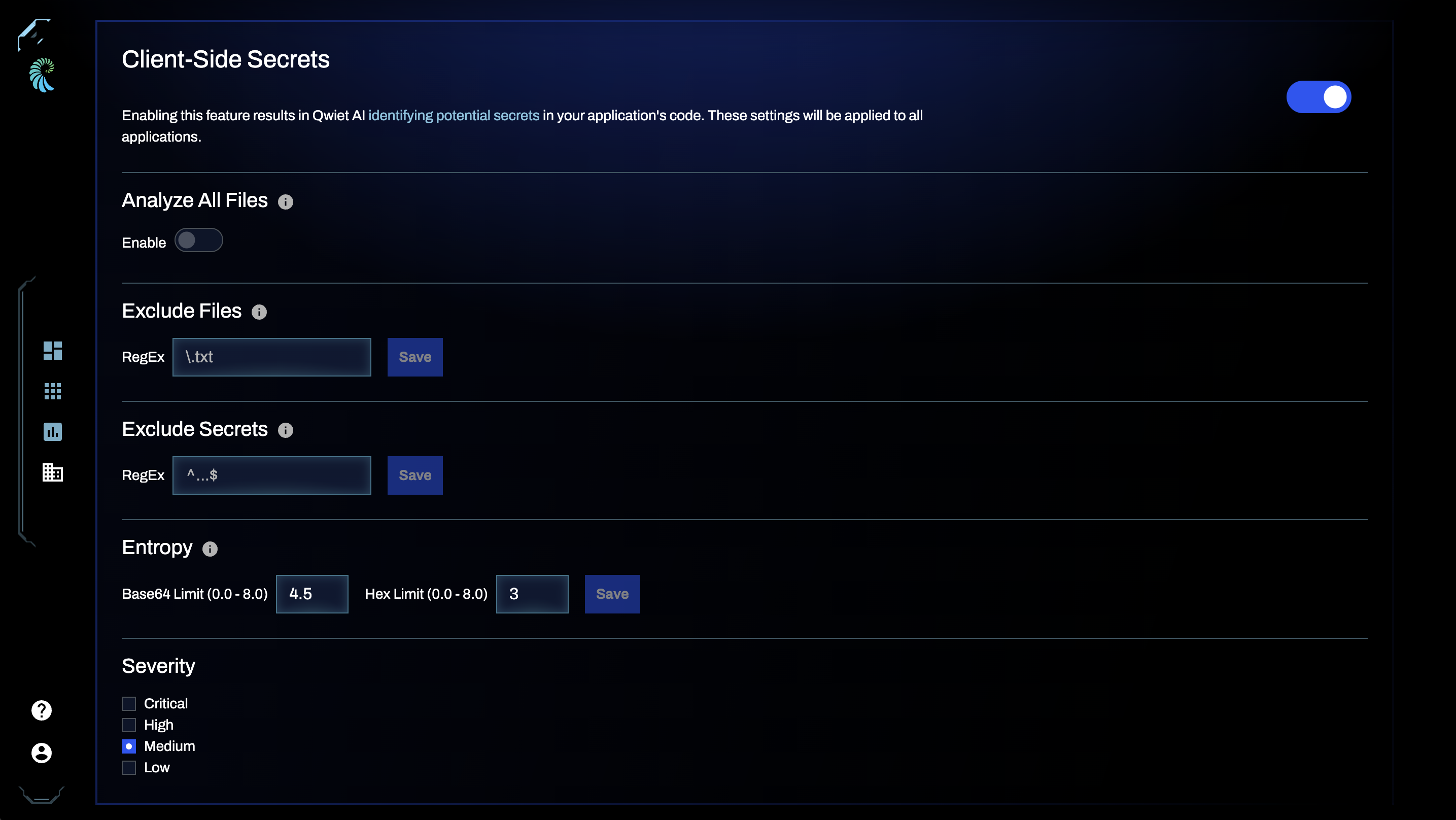
There are several settings available which may be used to customize the behavior of the secrets analysis process. These settings can be found in the Client-Side Secrets section of the Organization Settings and Application Settings pages. Qwiet recommends changing these settings only as needed, and ideally only at the application level instead of simply using the same settings across the entire organization.
Available settings:
- Analyze All files: When enabled, Qwiet preZero will consider all files in the directory being analyzed, even if they are not checked-in in a repository
- Exclude Files: Regular expression for which filenames to exclude from the
analysis. E.g.
.txtwould exclude all .txt files - Exclude Secrets: Regular expression for which secret values to exclude from
the results. E.g.
^...$would exclude all three-letter secrets - Exclude Lines: Regular expression for which lines to exclude from the analysis.
E.g.
^.*_key\s*=\s*.*$would exclude all lines with anything before_keyand after=, such asmy_variable_key = some_value - Entropy: Defines the entropy threshold for base64-encoded strings and HEX strings. See more details in the next section titled Entropy settings
- Severity: Defines the severity for findings produced by the Secrets analysis
- Plugins: Enable or disable detection plugins.
The settings can also be applied via environment variables:
| Parameters | Description |
|---|---|
QWIET_EXTERNAL_SECRETS_ALL_FILES | Scan all files in the project directory instead of just checked-in files. |
QWIET_EXTERNAL_SECRETS_MAX_CORES | Maximum number of CPU cores to be used for scanning secrets, defaults to 2. |
QWIET_EXTERNAL_SECRETS_BASE64_LIMIT | Entropy limit for high entropy strings. This value must be between 0.0 and 8.0, defaults to 4.5. |
QWIET_EXTERNAL_SECRETS_HEX_LIMIT | Entropy limit for high entropy strings. This value must be between 0.0 and 8.0, defaults to 3.0. |
QWIET_EXTERNAL_SECRETS_EXCLUDE_FILES | Regular expression for which filenames to exclude from the analysis. E.g. \.txt would exclude all .txt files. |
QWIET_EXTERNAL_SECRETS_EXCLUDE_SECRETS | Regular expression for which secret values to exclude from the results. E.g. ^...$ would exclude all three-letter secrets. |
QWIET_EXTERNAL_SECRETS_EXCLUDE_LINES | Regular expression for which lines to exclude from the analysis. E.g. ^.*_key\s*=\s*.*$ would exclude all lines with anything before _key and after =, such as my_variable_key = some_value. |
QWIET_EXTERNAL_SECRETS_DISABLE_PLUGIN | Comma-separated list of plugins to disable. E.g. Base64HighEntropyString. |
Entropy settings
One way to uncover secrets is by scanning for high entropy strings within the codebase. This is because passwords and other secrets are (or should be) strings of random characters, where completely random strings would have high entropy and completely predictable strings would have low entropy.
To put this into numbers, the Shannon entropy formula might be used to calculate the entropy of a specific string of symbols (characters).
The implementation used for detecting secrets will calculate a similar measure and will output numbers between 0 and 8.
If the entropy of a specific string surpasses the predefined threshold, it will be flagged as a potential secret. While this threshold can be adjusted, it is generally recommended to stick with the default settings, which have been set to a generally useful level of sensitivity. Lowering the threshold could result in numerous false positives, whereas increasing it might risk missing some leaked secrets.
As an additional example, the string aaaaaaaaaaaaaaaaaaaaaaa, while
very long, does not have high entropy and the detector for high-entropy
hex-encoded strings would not flag it based on the calculated entropy
value of 0.0. At the same time, the string
2b00042f7481c7b056c4b410d28f33cf has similar length, but is much more
random and the same detector would flag it as a potential secret based
on the calculated entropy value of 3.54. Note that the numbers given
are for reference only, adjusting the values for scanning should solely
be done based on the number of potential secrets flagged vs. any false
positives.
Viewing your results
The secrets that Qwiet identifies in your application will appear in the Vulnerabilities Dashboard.
To access your results:
- Log in to the Qwiet Dashboard
- In the list of Applications, find the one you're interested in and click to open.
You will see a summary page of all vulnerabilities identified by Qwiet, including secrets.
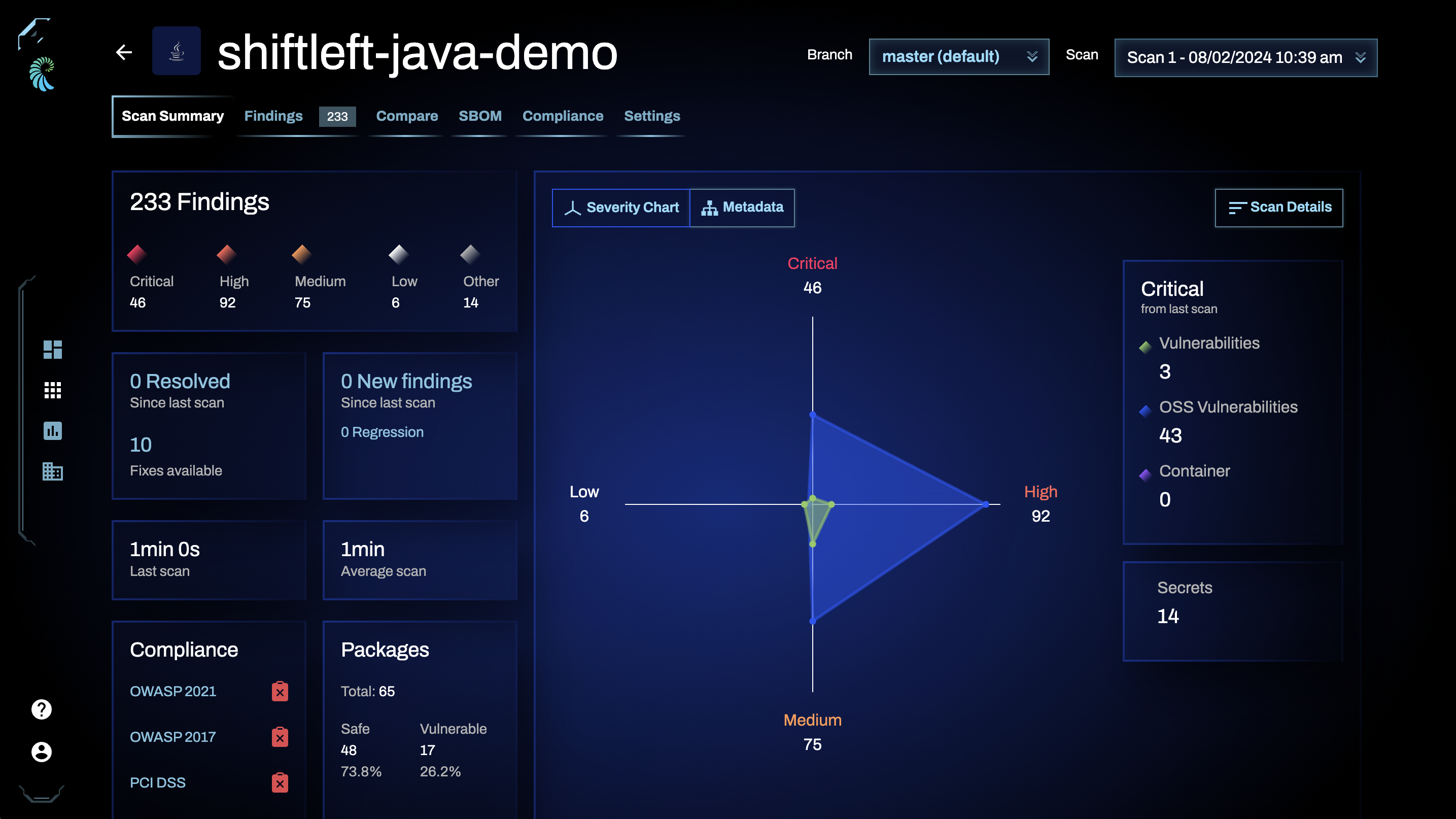
Click the Findings tab to display a list of the issues identified. You can also uncheck other findings types and filter the list down to just secrets.
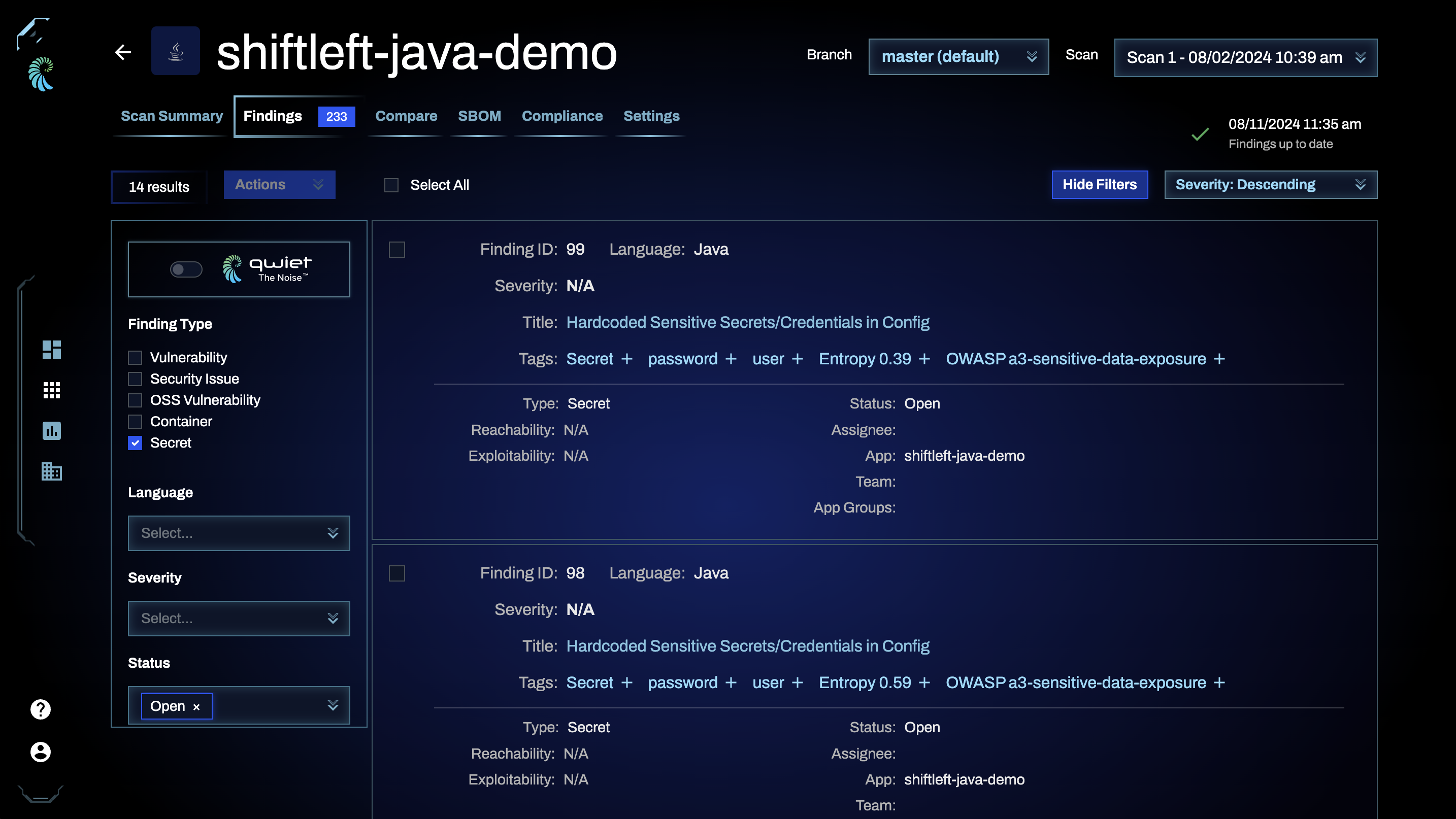
You can also filter the results based on:
- Its Status (which reflects any work that's been done by your team on the issue)
- Who it is Assigned to for further action
- One or more Advanced Filter, which allows you to specify the category (both general and OWASP) and the language of the code
False Positives
The heuristics to detect secrets will necessarily result in some False Positives. There are several ways to exclude these, as already mentioned in the Settings section above:
QWIET_EXTERNAL_SECRETS_EXCLUDE_FILESis the coarsest way to exclude entire files from the analysisQWIET_EXTERNAL_SECRETS_EXCLUDE_SECRETSlets you exclude specific secrets, or generally any pattern of secretsQWIET_EXTERNAL_SECRETS_EXCLUDE_LINESlets you exclude an entire line from the analysisQWIET_EXTERNAL_SECRETS_DISABLE_PLUGINlets you disable plugins- inline declarations
The last point requires modifying the source code in question:
Add pragma: allowlist secret at the end of a line to exclude it from
the results. Usually this requires the text to be in a comment, such
as:
MY_VARIABLE = 'my very secret secret' # pragma: allowlist secret
It's also possible to exclude the next line by adding
pragma: allowlist nextline secret instead:
// pragma: allowlist nextline secret
const Foo = "another secret here";