Roles-based access control
The Qwiet dashboard allows you to collaborate with others regarding any security vulnerabilities identified. You can view vulnerabilities on a per-application basis, assign findings for review/follow-up, communicate with one another regarding specific vulnerabilities, and more.
Depending on their assigned roles, users can view different data and perform various actions in Qwiet.
Roles-based access control (RBAC)
Roles-based access control (RBAC) is the practice of assigning permissions to users based on their role within an organization. Because RBAC eliminates the need to set permissions individually, you get a more straightforward access management approach that's less error-prone.
RBAC in Qwiet preZero
There are several concepts you should be familiar with when working with Qwiet preZero's role-based access control (RBAC) feature:
-
A team is a group of users and applications (e.g., Team A consists of Alice, Bob, and Charlie and App1, App2, and App3).
-
All users must have a role in your organization
-
A user can belong to one or more teams. If a user belongs to more than one team, they must be assigned a role in the context of each team to which they belong. The roles do not have to be the same (e.g., Alice is an admin for Team A, whereas she is a member in Team B).
-
Roles that you assign to users are additive; this means that the user can do everything their organization role permits and their team roles permit.
-
Organization roles allow users to perform actions on an organizational level (e.g., log in to the organization and read basic information about the organization). However, this does not grant access to apps by default; the user must be assigned to one or more teams to see apps.
Roles
There are organization roles and team roles available.
Organization roles
| Role | Description |
|---|---|
| Super Admin | Permitted all actions except deleting the organization and deleting/demoting other super admins. Can add applications. |
| Power User | Permitted all app-related actions (including adding and deleting apps). Can add apps. |
| Member | Permitted all finding-related actions. Cannot destroy data (e.g., delete apps) and is limited to updating findings metadata. |
| Guest | Can view findings-related information. |
| Team Defined | Can log into the organization, but cannot access any data unless added to a team. |
| Collaborator | Deprecated. Orgs created after the release of RBAC will not be shown this option. Can perform any non-destructive action. |
Team roles
| Role | Description |
|---|---|
| Team Admin | Permitted all app-related actions (including deleting apps) for their team. Can add apps to their teams and move apps from one team to another, as long as they are a team admin for both teams. |
| Team Manager | Permitted all app-related actions (except deleting apps) for their team. Can add apps to their teams and move apps from one team to another, as long as they are a team manager for both teams. |
| Team Member | Can perform findings-related actions, but cannot destroy data (e.g., delete apps). Can update findings metadata. |
| Team Developer | Same as Team Member. Can also submit applications for analysis. |
| Team Guest | Can view findings-related data. |
Sample usage
The following examples will show how organization roles and team roles work and how the permissions granted to a user are additive.
Example 1
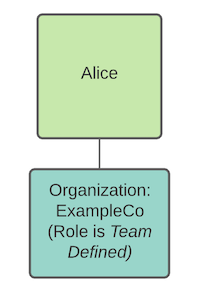
Alice is assigned to the ExampleCo org as team defined in this example. In this case, she can log into Qwiet, but she will not be able to see any applications, findings, and so on.
Example 2
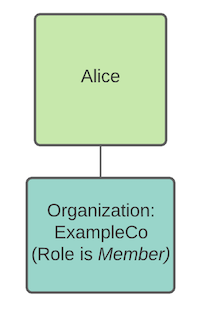
Alice is assigned to the ExampleCo org as a member in this example. She can see all applications, including findings data, but she can only modify the findings metadata.
Example 3
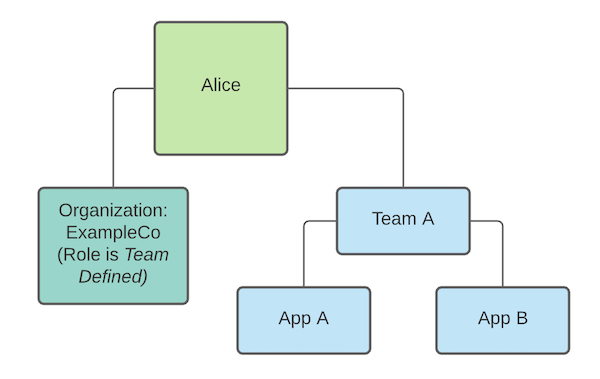
In this example, Alice is granted a team defined role, granting her permission to log in to the organization. She is also a member of Team A, allowing her access to Apps A and B.
Custom Roles
Custom Roles gives administrators the flexibility to create their own roles with specific sets of permissions. This allows organizations to grant users the exact level of access they need to perform their duties, whether at the organization or team level. Organizations can have a maximum of 10 custom roles.
Creating a Custom Role
To create a new custom role, follow these steps:
- Navigate to Manage Roles in Organization Settings.
- Click on the + Create Role button.
- Select the Resource Type:
- Organization: These roles grant permissions across the entire organization.
- Team: These roles grant permissions only within a team's context.
- Provide a Role Name and a Role Description:
- Role Name: Give your role a clear and descriptive name, such as "Security Auditor" or "Developer".
- Role Description: Briefly explain the purpose of the role to help others understand its intended use.
- Assign Scopes:
- Scopes are individual permissions that you can assign to the role. Select the scopes that correspond to the actions you want users with this role to be able to perform. For a detailed list of available scopes, see the "Available Scopes" section below.
- Save the Role: Once you're satisfied with your configuration, click Create Role to create the new custom role.
Available Scopes
Here is a list of all the scopes you can use to build your custom roles. They are grouped by their general function to help you find what you need.
Application Management
app_group:delete: Allows deleting application groups.app_group:update: Allows updating application groups.apps:list: Allows listing applications.project:archive: Allows archiving a project.project:create: Allows creating a new project.project:delete: Allows deleting a project.project:read: Allows viewing project details.project:update: Allows updating project settings.
Authentication & Access
auth_provider:*: Grants full access to authentication providers.kontra:login: Allows to log in to Kontra.kontra:read: Allows reading Kontra-related data.saml_config:create: Allows creating SAML configurations.saml_config:delete: Allows deleting SAML configurations.saml_config:list: Allows listing SAML configurations.saml_config:update: Allows updating SAML configurations.
AutoFix
autofix:read: Allows reading AutoFix suggestions.autofix:request: Allows requesting an AutoFix suggestion.autofix_pat:read: Allows to read Personal Access Tokens used to create AutoFix Pull Requests.autofix_pat:write: Allows to manage Personal Access Tokens used to create AutoFix Pull Requests.
Findings & Vulnerabilities
finding_assign:update: Allows assigning a finding to a user.finding_comment:create: Allows adding comments to findings.finding_comment:list: Allows listing comments on findings.finding_comment:read: Allows reading comments on findings.finding_fixed:update: Allows marking a finding as fixed.finding_ignore:update: Allows ignoring a finding.finding_status:update: Allows updating the status of a finding.findings:create: Allows creating new findings.findings:list: Allows listing all findings.findings:read: Allows viewing the details of a finding.findings:update: Allows updating findings.sca:read: Allows reading Software Composition Analysis (SCA) data.vuln_assign:write: Allows assigning vulnerabilities.vuln_status:write: Allows updating the status of vulnerabilities.vulns:read: Allows reading vulnerability data.
Integrations
azureboard_association:read: Grants access to read Azure Boards project associations for applications.azureboard_association:write: Allows creating or modifying Azure Boards project associations for applications.azureboard_auth:write: Permits configuring Azure Boards authentication for the organization.azureboard_workitem:read: Grants access to read Azure Boards work items linked to findings or projects.azureboard_workitem:write: Allows creating or updating Azure Boards work items from findings or projects.github:install: Allows installing the GitHub integration.github_fork_demo:create: Allows creating a demo by forking on GitHub.github_repos:list: Allows listing connected GitHub repositories.github_user_repo:create: Allows creating a repository for a user on GitHub.jira_app:write: Allows writing to the Jira application.jira_association:create: Allows creating associations with Jira.jira_association:read: Allows reading associations with Jira.jira_issue:read: Allows reading Jira issues.jira_issue:write: Allows writing to Jira issues.scim:create: Allows creating SCIM resources.scim:delete: Allows deleting SCIM resources.scim:read: Allows reading SCIM resources.scim:update: Allows updating SCIM resources.slack:update: Allows updating Slack integration settings.
Organization & Team Management
org:update: Allows updating organization settings.org_audit_trail:read: Allows reading the organization's audit trail.org_configuration:read: Allows reading the organization's configuration.org_configuration:write: Allows writing to the organization's configuration.org_invitations:create: Allows creating new user invitations.org_invitations:delete: Allows deleting pending user invitations.org_invitations:list: Allows listing user invitations.org_user:delete: Allows deleting a user from the organization.org_user:list: Allows listing all users in the organization.org_user:update: Allows updating a user's details.roles:create: Allows creating new roles.roles:delete: Allows deleting existing roles.roles:list: Allows listing all roles.roles:update: Allows updating existing roles.scopes:list: Allows listing all available scopes.team_apps:update: Allows updating the applications associated with a team.team_memberships:update: Allows updating team memberships.teams:create: Allows creating new teams.teams:delete: Allows deleting teams.teams:list: Allows listing all teams.teams:read: Allows viewing team details.teams:update: Allows updating team settings.
Scans & Analysis
check_analysis_configuration:list: Allows listing check-analysis configurations.check_analysis_configuration:read: Allows reading check-analysis configurations.check_analysis_configuration:write: Allows creating or changing check-analysis configurations.cold_start_subscription:read: Allows reading cold start subscription details.cold_start_subscription:update: Allows updating cold start subscriptions.org_inspect_configuration:create: Allows creating inspect configurations for the organization.org_inspect_configuration:validate: Allows validating inspect configurations.org_runs:create: Allows initiating new runs for the organization.org_runs:read: Allows reading the results of organization runs.pipelinestatus:read: Allows reading the status of the pipeline.scan_status:update: Allows updating the status of a scan.scans:create: Allows initiating new scans.scans:read: Allows reading scan results.uploads:write: Allows uploading results and other artifacts.
System & General
blocked_seats:list: Allows listing blocked seats.blocked_seats:update: Allows updating blocked seats.log:write: Allows writing to logs.metrics:write: Allows writing metrics.org_alert_notification:read: Allows reading organization alert notifications.org_alert_notification:update: Allows updating organization alert notifications.org_backup:read: Grants access to view organization backups and retrieve backup download links.org_metrics:read: Allows reading organization metrics.org_user_notification:create: Allows creating user notifications.org_user_notification:delete: Allows deleting user notifications.org_user_notification:read: Allows reading user notifications.org_user_notification:update: Allows updating user notifications.policies:customer: Relates to customer-specific policies.reports:read: Allows reading reports.seats:claim: Allows claiming a seat.seats:delete: Allows deleting a seat.seats:list: Allows listing all seats.seats:write: Allows writing to seat data.subscriptions_trial:update: Allows updating trial subscriptions.tokens:create: Allows creating integration tokens.tokens:delete: Allows deleting integration tokens.tokens:list: Allows listing integration tokens.versions:read: Allows reading version information.webhook:read: Allows to read the webhook configuration and eventswebhook:write: Allows to manage the webhook configuration