Findings
The findings tab of the application page allows you to see the findings discovered during preZero analyses. Currently, preZero identifies the following types of findings: vulnerabilities, OSS vulnerabilities, container findings, secrets, and security issues.
For each finding on the list, you'll see the following fields:
- Finding ID (e.g.
42) - Severity level (e.g.,
Critical) - Title (e.g.
SQL Injection: Attacker-controlled Data Used in SQL Query) - Tags (e.g.,
OWASP a1-injectionorCVSS 9) - Type (e.g.
Vulnerability,Secret) - Status (e.g.,
Fixed) - Reachability:
Reachable,Unreachable, orN/A - Exploitability:
Exploitable,No Exploits, orN/A - App name (e.g.
shiftleft-java-demo) - Team name (e.g.
Engineering) - App groups (e.g.
Code Science)
You can sort your list based on Finding ID or Severity level (ascending or descending).
Right above the sorting options, on the top-right corner, you can see whether or not there are new SCA results available. Qwiet preZero continually checks your application and alerts you if there are new OSS vulnerabilities affecting your application. The timestamp displayed lets you know when the latest check for new OSS vulnerabilities was performed by Qwiet. If there are new results, you should rescan your application to populate the findings to the dashboard.
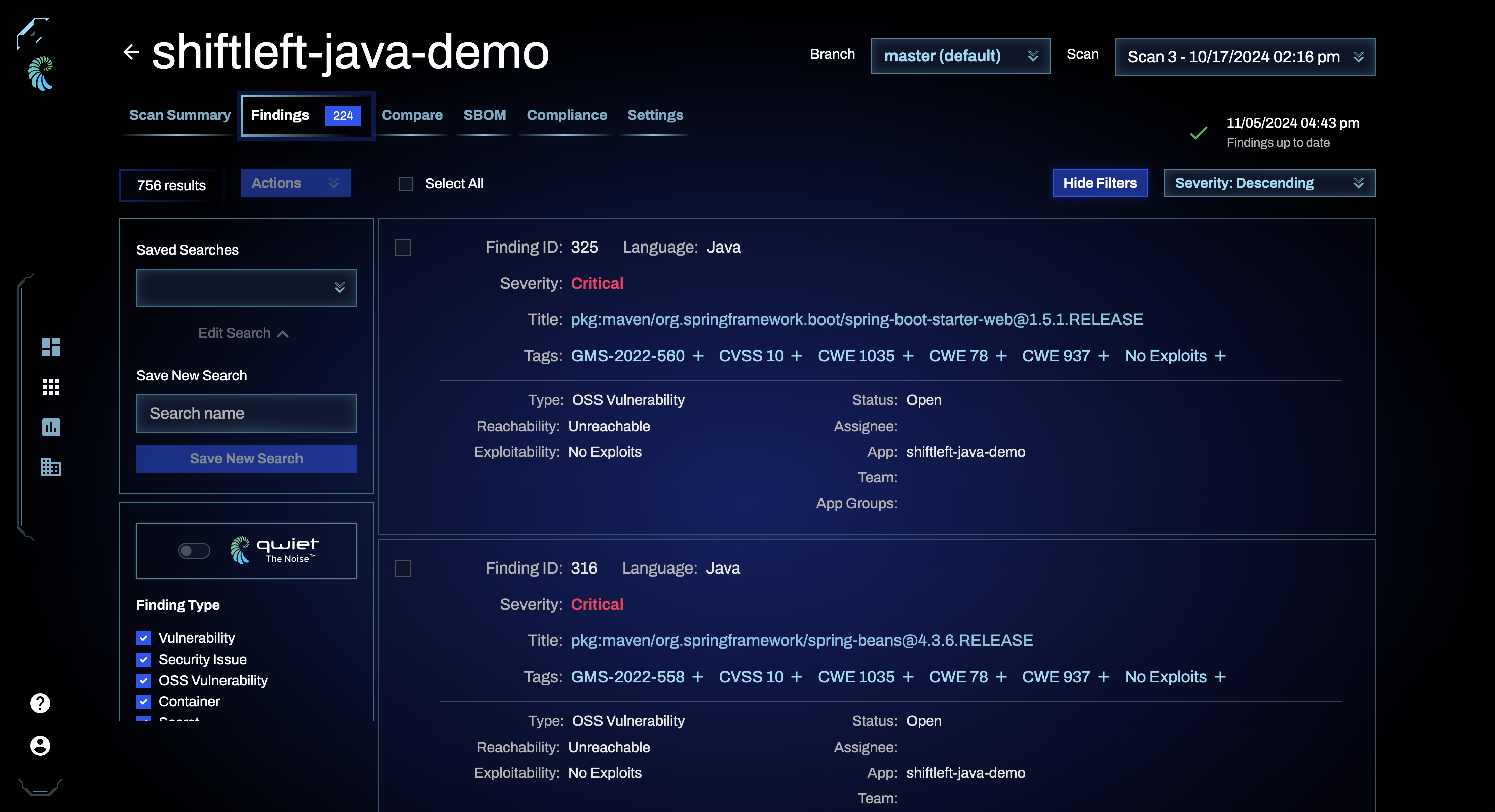
Qwiet the Noise
To help prioritize the review and fixing of findings, you can toggle on Qwiet the Noise, which filters for only critical, high, reachable (if applicable), and exploitable (if applicable) findings.
Filtering findings
You can filter the findings list by the following criteria:
- Finding Type
- Language
- Severity
- Status
- Assigned To
- AutoFix
- Exploitability
- Reachability
- CVSS Score
- EPSS Score
- Package Group
- Package Component
- OWASP 2021 Category
- OWASP Category
- CWE Category
- CVE
- Category
The Saved Searches panel allows you to save and recall a set of filters. Each user can save up to 10 searches. Once a search is recalled, it can also be edited and deleted as needed.
To quickly remove all filters, click on the Findings tab title.
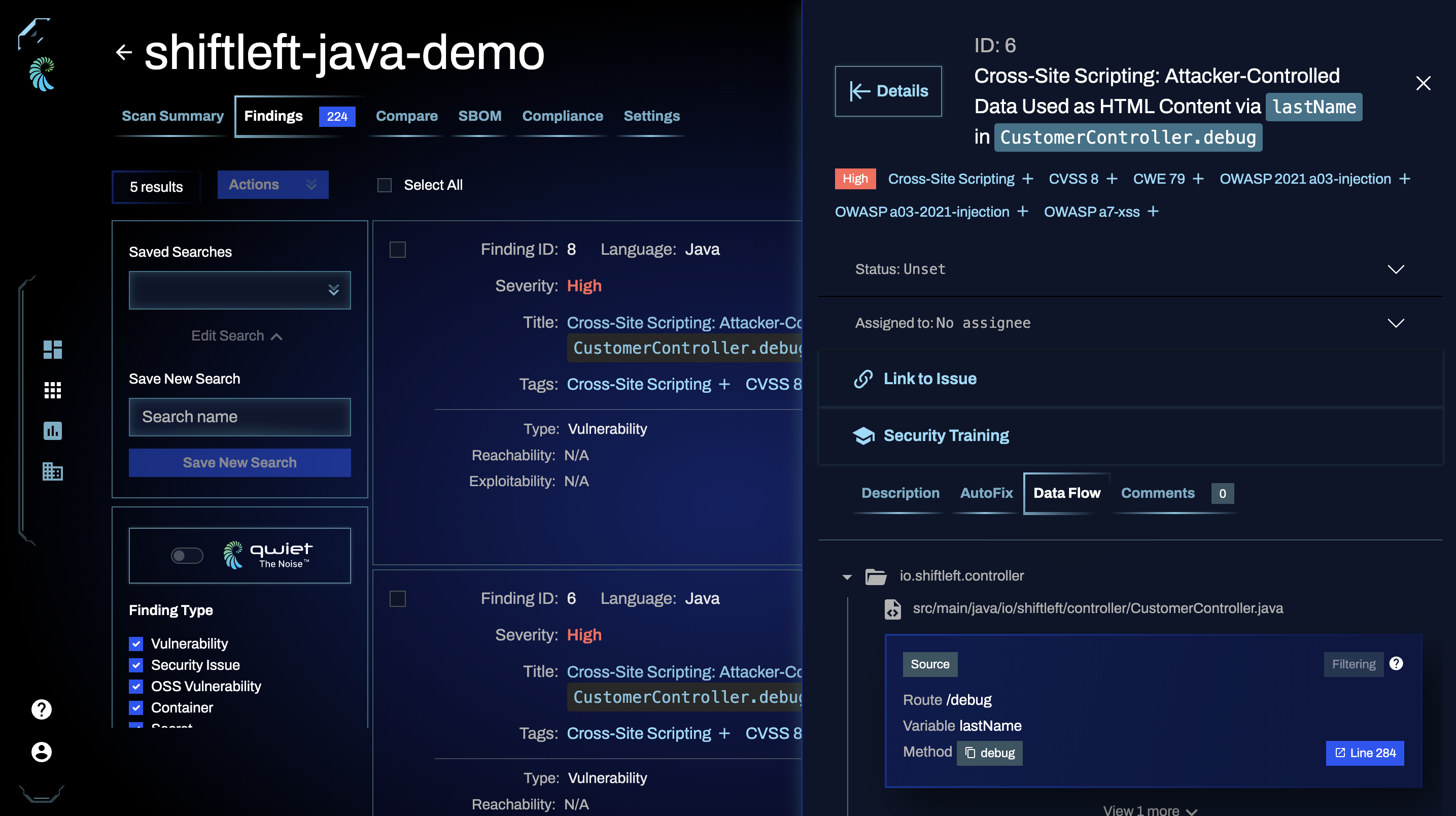
Viewing detailed finding information
Clicking on a finding in your results list will open a new window pane on the right with detailed information. Note that some tabs are only available for some findings types (e.g. SAST), and only when certain capabilities are enabled (e.g. AutoFix).
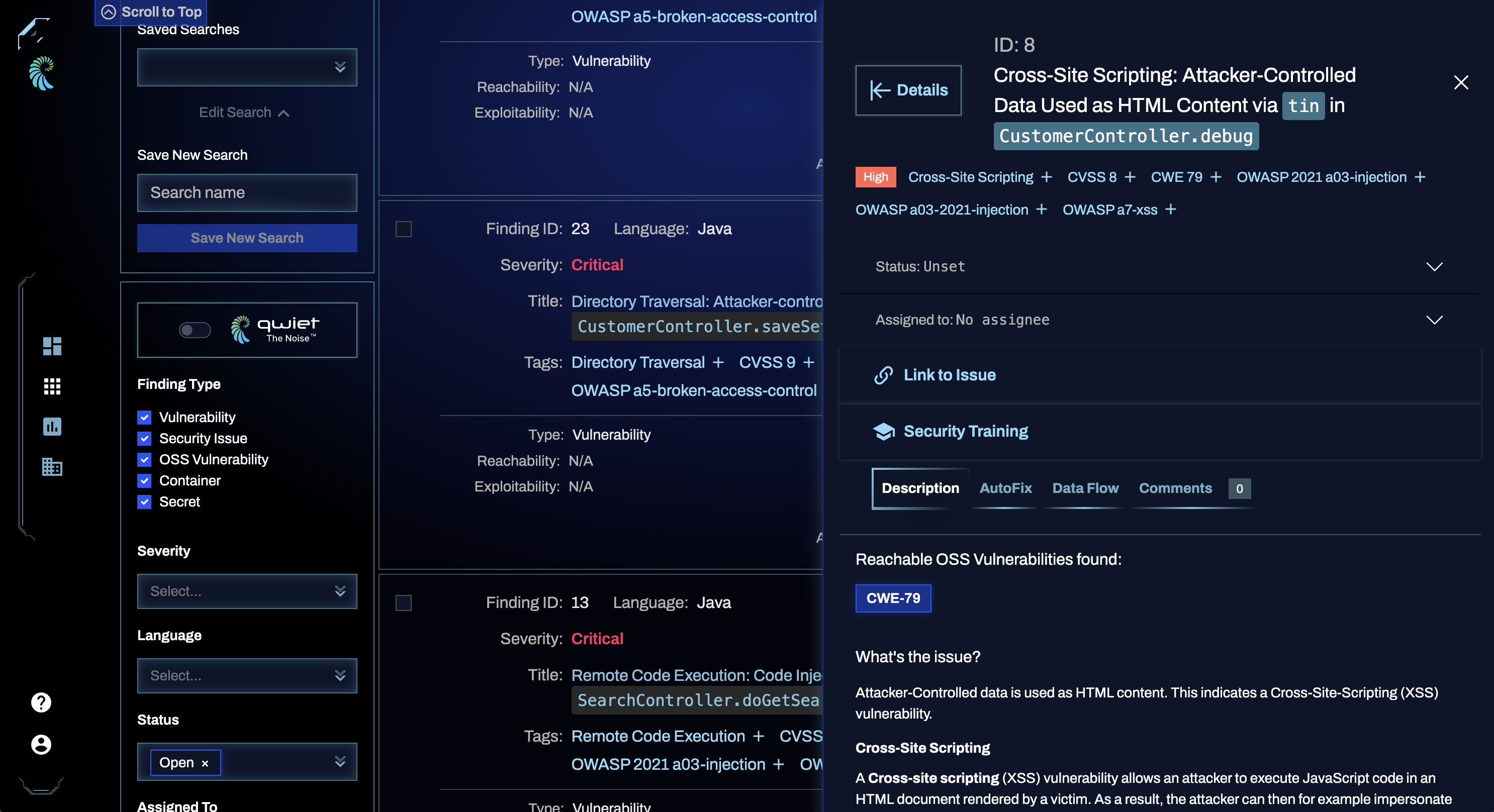
-
Description: the description tab features an in-depth write-up of what the issue is and why it is a problem, as well as mitigation suggestions for securing your app.
-
AutoFix: if enabled for your organization and application, this tab shows available AutoFix suggestions, AutoFix pull request link (if enabled and available), and additional information that you can use to address a SAST finding.
-
Data Flow: the data flow tab shows you the path from the source (which is the portion of the code that "allows" a vulnerability to occur) to the sink (where the vulnerability happens).
For example, suppose the vulnerability is a command injection vulnerability. The source could be a function accepting user input, while the sink would be where a command execution occurs using the user input. The data flow is the path between these two spots in the code.
-
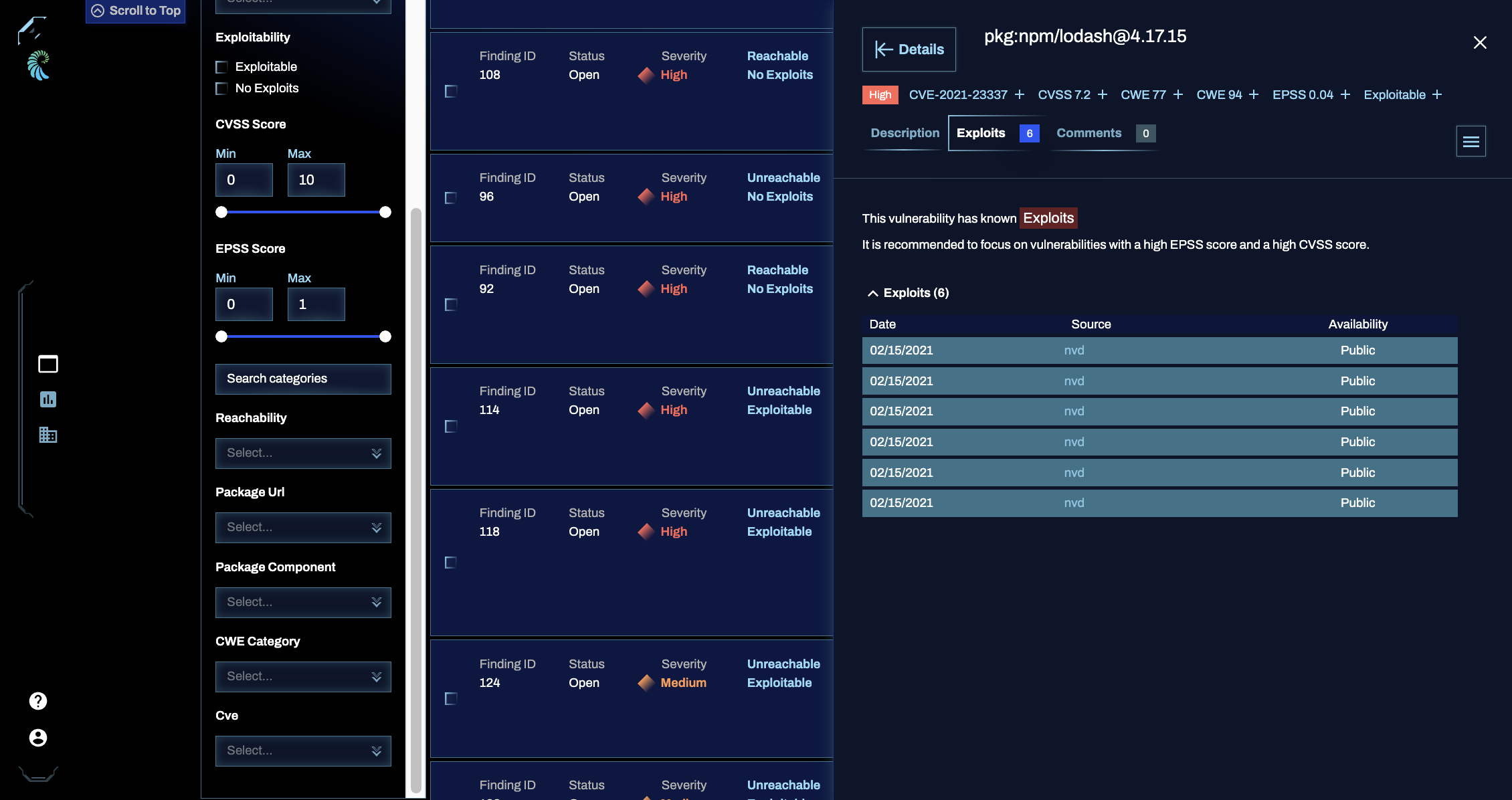
Exploits (Blacklight): the exploits tab includes up-to-date exploitability information on the vulnerability, including the:
- Date reported
- The source providing a proof of concept of the exploit
- The availability of the exploit (e.g., public, private, or commercial)
The Exploit Prediction Score System (EPSS) score shown for the vulnerability can help you determine the severity and priority of a given vulnerability. The EPSS score falls between 0 and 1, and we recommend focusing on findings with a high EPSS score and high CVSS score. The presence of a CISA KEV tag indicates that the vulnerability is part of the United States of America's Cybersecurity & Infrastructure Security Agency (CISA)'s Known Exploited Vulnerabilities Catalog (KEV). This can help you determine the importance of an OSS finding.
-
Comments: the comments tab allows you and your team members to make notes specifically about this finding; if there are multiple comments for this finding, Qwiet displays them in reverse chronological order.
Filtering by sources and sinks
Using the filter by sources/sinks feature available in the Data Flow tab or panel (see Expanded details below), you can triage vulnerabilities faster and determine which findings your code fixes would affect.
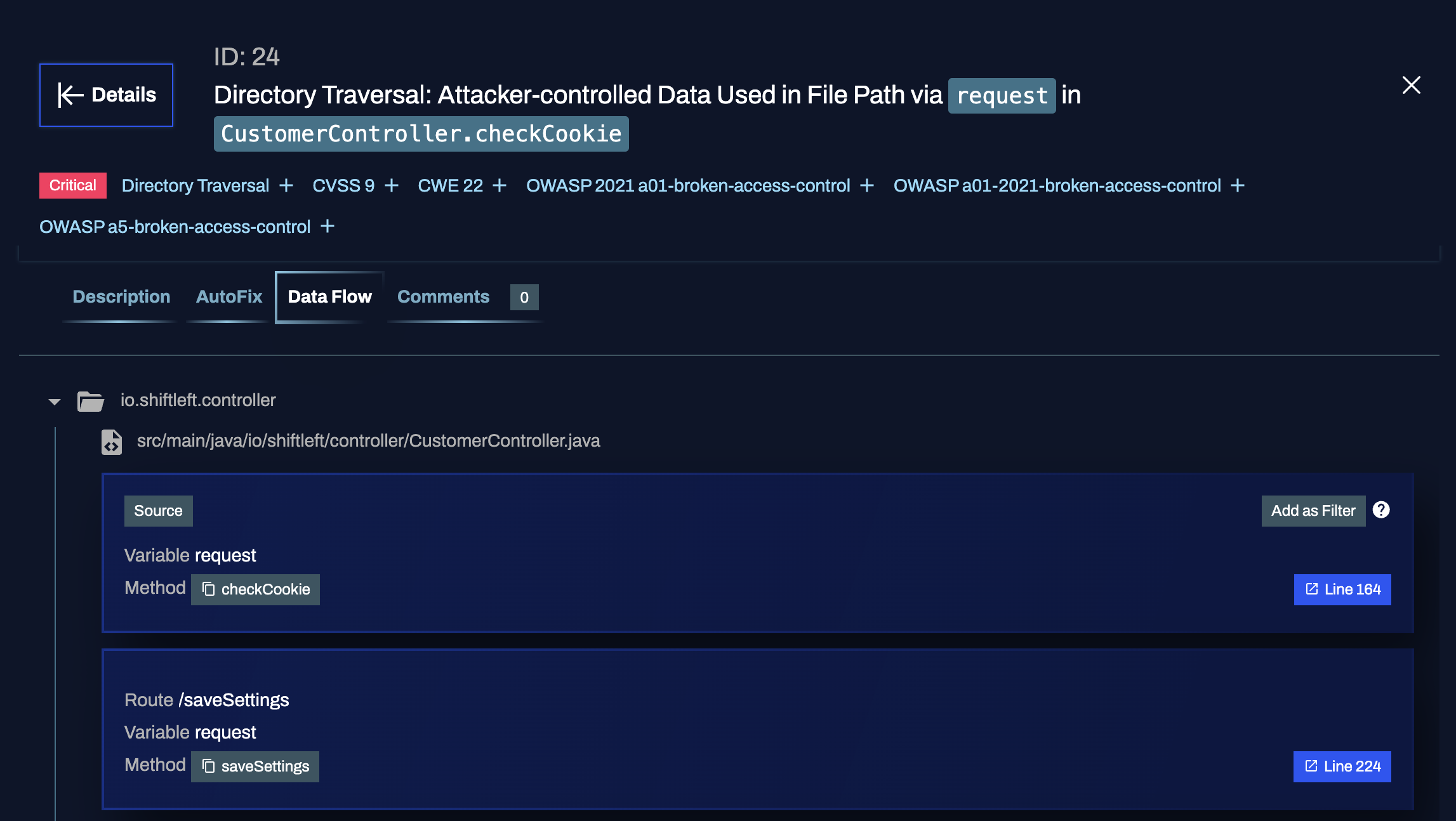
For each source/sink identified by Qwiet preZero, you'll see an option to Add as Filter.
When set, you'll notice that the vulnerabilities list updates to only include vulnerabilities that feature that same source/sink. If you were to patch that specific code portion, these would be the vulnerabilities affected by your code change.
Expanded details
Click Details in the top-left corner of the Finding panel to switch to an expanded view of the finding. This allows you to see data side by side and make quick decisions on how to address a finding.
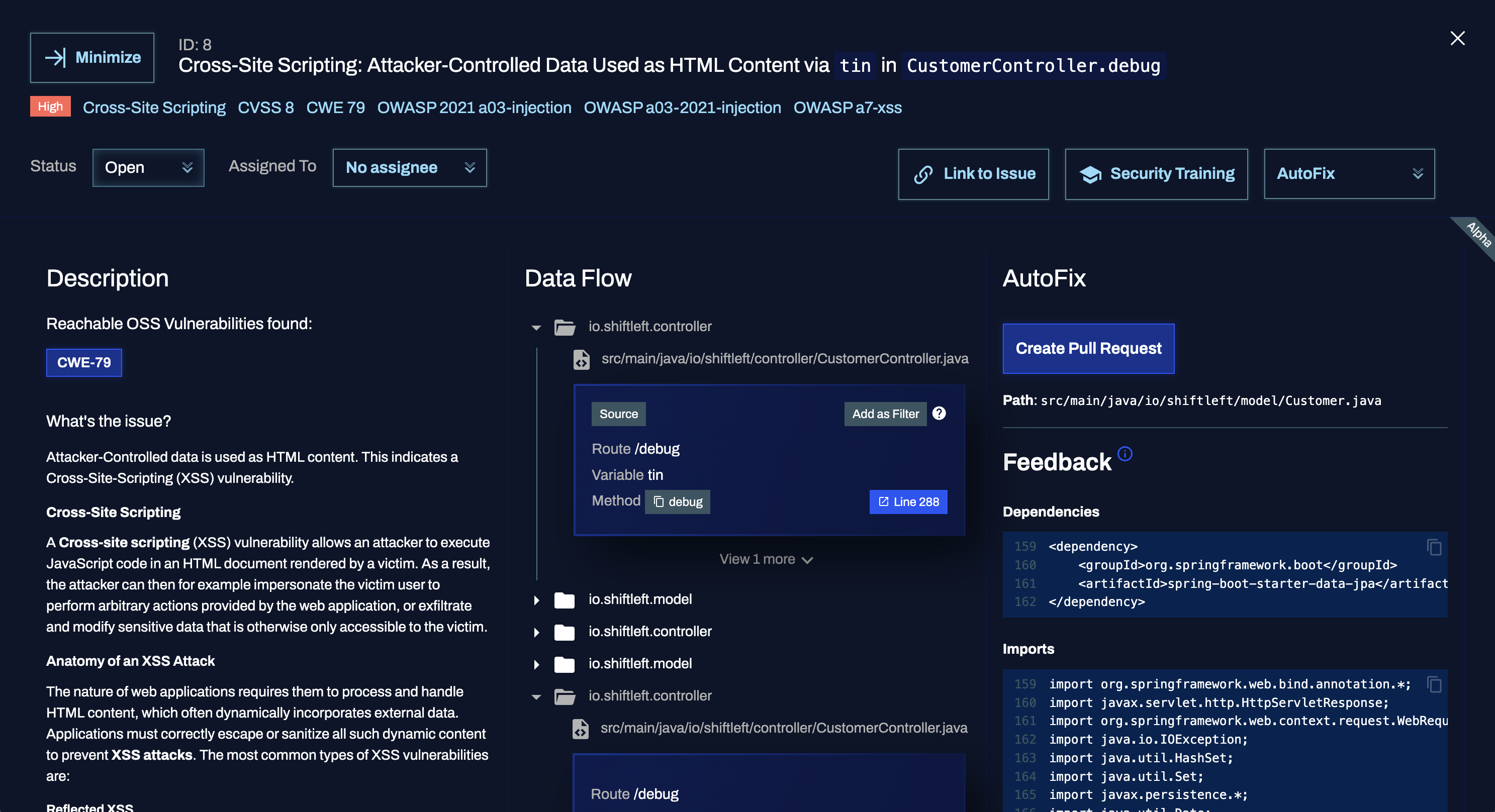
To return to the summary view, click Minimize in the top-left.
Changing status
Set the finding status to reflect work that's been done (e.g., set the finding status to Fixed if you've mitigated the issue):
- Open: The default status value for a finding
- Fixed: Mark the finding as fixed if you've applied remediation of some type (note that setting this status does not fix the finding) so that Qwiet doesn't include the finding in the scan results
- Ignored: Mark the finding as ignored so it doesn't show up in scan results again. Used to indicate that something is a false positive or is unlikely to impact the application's security. If you set the status to ignored, you must also provide a comment that includes information on your reasoning for choosing this status
- 3rd Party: Mark the finding as 3rd Party to indicate that the finding is in a third-party library; you can't fix the finding at the moment, but you should return to it at a later date
Additional actions
You can also perform the following actions:
- Assign to a team member the vulnerability for further research and work
- Get a link to issue that's specific to this finding that you can share with others
- Launch Security Training that's specific to this type of finding (if available and applicable)
- Click the Send to Jira button (if the Jira integration is enabled) to create a Jira issue with the finding details