Azure DevOps
This article shows you how to integrate Qwiet preZero into your Azure DevOps workflow to provide automated code analysis. We provide two sets of instructions based on how you define your Azure pipelines: using YAML syntax or the Classic interface.
- YAML
- Classic
For Azure Pipelines defined using YAML syntax
This tutorial assumes that you have an existing YAML-base Azure Pipeline defined. You will be adding the tasks required to integrate preZero to this file.
Step 1: Create your secret variables
You will need to create secret variables to store authentication information for Qwiet.
We recommend creating your secret variables using variable groups since this method balances security with ease of deployment across multiple repositories.
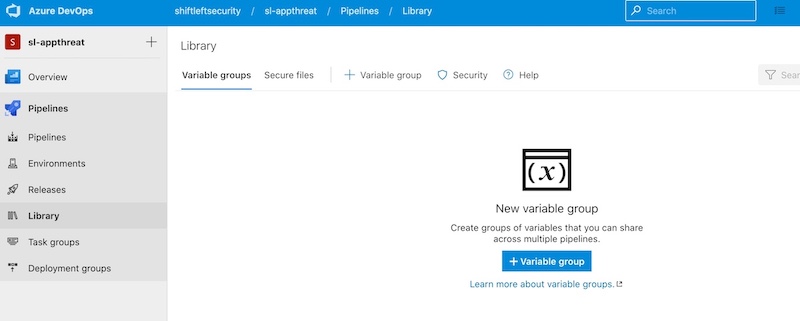
However, you could also create your secret variables using:
When creating a variable group, we recommend calling it something like shiftleft-token. You can then provide your access token as SHIFTLEFT_ACCESS_TOKEN.
When running in a production environment, we recommend that you use a CI config token as the access token. You can create your CI config token in the Qwiet Dashboard.
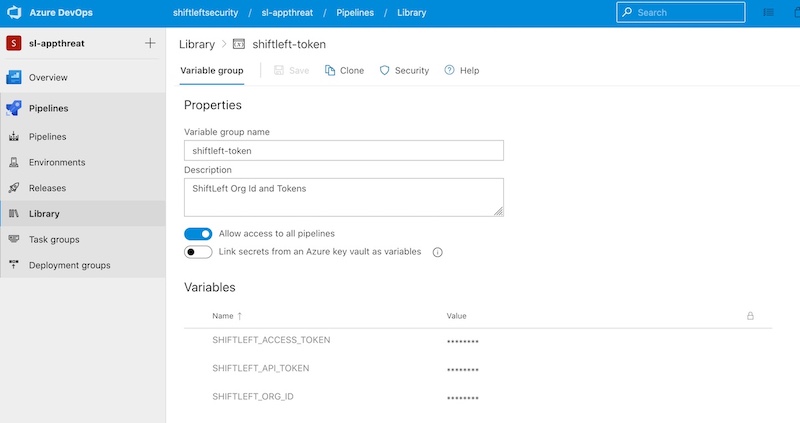
At this point, you can refer directly to this group in the pipeline's YAML configuration file using the group property under the variables section.
variables:
- group: shiftleft-token
Step 2: Add Qwiet to your pipeline
You will need to include instructions in your Pipeline to download the Qwiet CLI so that the Pipeline can run preZero.
If you're running Windows, you can do so using a PowerShell task:
- task: PowerShell@2
displayName: Download Qwiet cli
inputs:
targetType: 'inline'
script: |
Invoke-WebRequest -Uri 'https://cdn.shiftleft.io/download/sl-latest-windows-x64.zip' -OutFile $(Agent.HomeDirectory)\sl.zip
Expand-Archive -Path $(Agent.HomeDirectory)\sl.zip -DestinationPath $(Agent.HomeDirectory) -Force\
If you're running Linux or macOS, you can use a script task:
- task: CmdLine@2
displayName: Download Qwiet cli
inputs:
targetType: 'inline'
script: |
curl https://cdn.shiftleft.io/download/sl > $(Agent.HomeDirectory)/sl && chmod a+rx $(Agent.HomeDirectory)/sl
Step 3: Invoke preZero for code analysis
The following sections will show you how to analyze your Java or C# applications.
When invoking preZero, you need to refer to the SHIFTLEFT_ACCESS_TOKEN variable. As suggested earlier in this article, if you create a variable group, these variables will be available automatically to all of your Pipelines.
Analyzing a Java application
The following examples show how you can build your Java application (which is required before preZero can analyze your code), then use the Qwiet CLI to invoke preZero for code analysis.
Please note that the Qwiet CLI requires Java 8 to create the Code Property Graph (CPG) representation of your source code. This is necessary before code analysis unless you are analyzing a project written in C#. If so, you can skip this step.
To set up Java 8, use the Java Tool Installer.
- task: JavaToolInstaller@0
inputs:
versionSpec: '8'
jdkArchitectureOption: 'x64'
jdkSourceOption: 'PreInstalled'
On Windows:
- task: Maven@3
inputs:
mavenPomFile: 'pom.xml'
mavenOptions: '-Xmx3072m'
javaHomeOption: 'JDKVersion'
jdkVersionOption: '1.8'
jdkArchitectureOption: 'x64'
publishJUnitResults: false
goals: 'package'
- task: CmdLine@2
displayName: Analyze with preZero
inputs:
script: |
$(Agent.HomeDirectory)\sl.exe analyze --app ShiftLeftJavaAzWin --tag branch=$(Build.SourceBranchName) --java target/hello-shiftleft-0.0.1.jar
workingDirectory: '$(Build.SourcesDirectory)'
env:
SHIFTLEFT_ACCESS_TOKEN: $(SHIFTLEFT_ACCESS_TOKEN)
On Linux/macOS:
- task: CmdLine@2
displayName: Analyze with preZero
inputs:
script: |
$(Agent.HomeDirectory)/sl analyze --app ShiftLeftJava --tag branch=$(Build.SourceBranchName) --java target/hello-shiftleft-0.0.1.jar
workingDirectory: '$(Build.SourcesDirectory)'
env:
SHIFTLEFT_ACCESS_TOKEN: $(SHIFTLEFT_ACCESS_TOKEN)
Analyzing a C# application
The following examples show you how to build your .NET Core application, then use the Qwiet CLI to invoke preZero for code analysis.
- task: DotNetCoreCLI@2
displayName: Build console app
inputs:
command: 'build'
projects: '$(Build.SourcesDirectory)\netcoreConsole'
- task: CmdLine@2
displayName: Analyze with preZero
inputs:
script: |
$(Agent.HomeDirectory)\sl.exe analyze --app netcoreConsole --tag branch=$(Build.SourceBranchName) --csharp netcoreConsole/netcoreConsole.csproj
workingDirectory: '$(Build.SourcesDirectory)'
env:
SHIFTLEFT_ACCESS_TOKEN: $(SHIFTLEFT_ACCESS_TOKEN)
For .NET applications, pass in the .sln file instead of the .csproj file:
- task: CmdLine@2
displayName: Analyze with preZero
inputs:
script: |
$(Agent.HomeDirectory)\sl.exe analyze --app netfwWebapi --tag branch=$(Build.SourceBranchName) --csharp netfwWebapi/netfwWebapi.sln
workingDirectory: '$(Build.SourcesDirectory)'
env:
SHIFTLEFT_ACCESS_TOKEN: $(SHIFTLEFT_ACCESS_TOKEN)
To pass additional information to Azure, you can use predefined variables that you then reference in the env block of your script.
Recursively finding and scanning your solution/project files
The following example shows you how to modify the sl analyze invocation to recursively find all .sln files and scan them with Qwiet:
# Recursively find all .sln files and scan them with Qwiet preZero
# Be sure to change the app.group value from "test-appgroup" to your preferred name
Get-ChildItem -Path . -Filter *.sln -Recurse -ErrorAction SilentlyContinue -Force | ForEach-Object {
sl.exe analyze --csharp --oss-project-dir $($_.Directory) --tag app.group=test-appgroup --app $($_.Name -replace '.sln', '') $($_.FullName)
}
Alternatively, you can recursively find and scan all .csproj files if .sln-based scans are taking too long:
# Recursively find all .csproj files and scan them with Qwiet preZero
# Use this when .sln based scans are taking too long
# Be sure to change the app.group value from ß"test-appgroup" to your preferred name
Get-ChildItem -Path . -Filter *.csproj -Recurse -ErrorAction SilentlyContinue -Force | ForEach-Object {
sl.exe analyze --csharp --oss-project-dir $($_.Directory) --tag app.group=test-appgroup --app $($_.Name -replace '.csproj', '') $($_.FullName)
}
For Azure Pipelines defined using the classic interface
If you haven't already, sign in to your Azure DevOps organization. Then, open up the project where you would like to configure your pipeline and navigate to the details page for your pipeline.
You need to create a series of tasks to execute each part of the code analysis workflow.
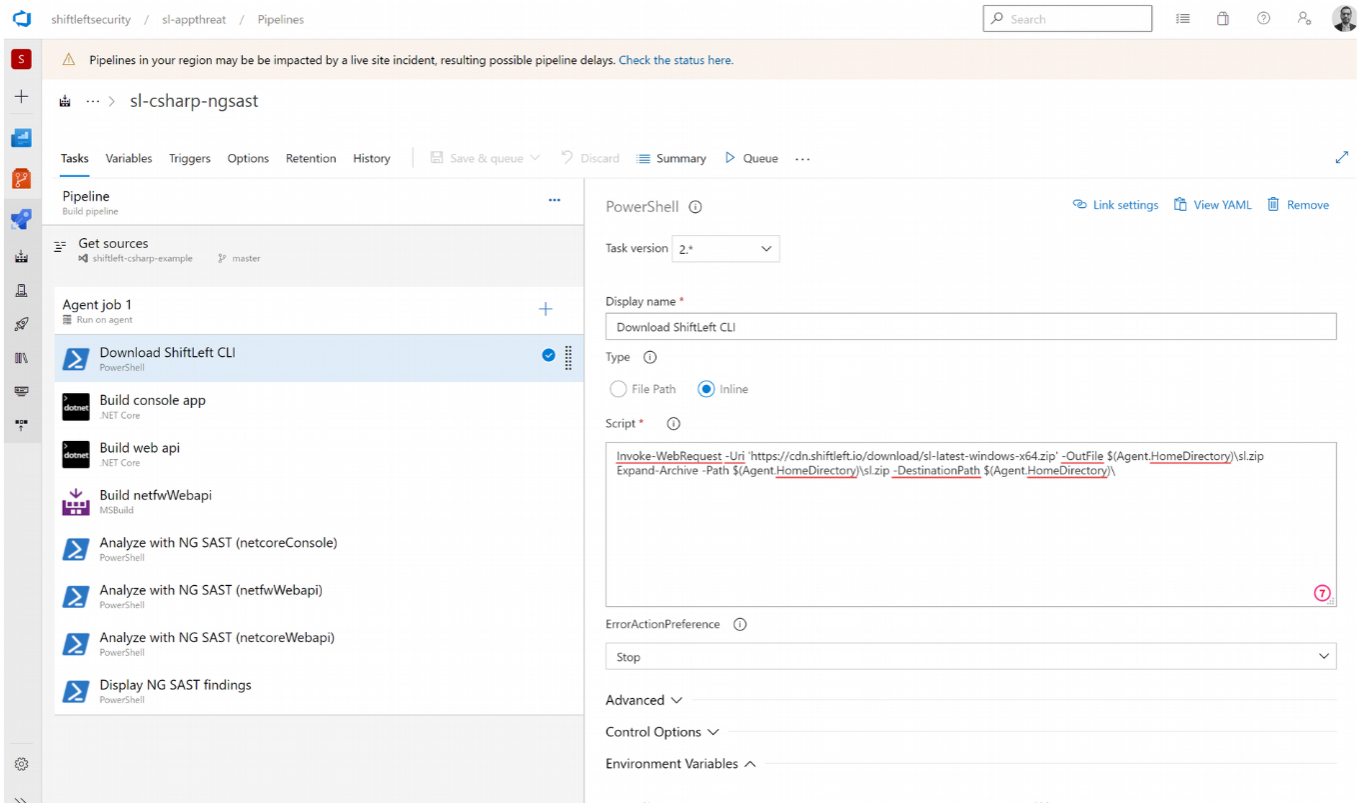
Step 1: Download preZero
First, create a task to download Qwiet. This will be an inline task, and under Script, provide:
Invoke-WebRequest -Uri 'https://cdn.shiftleft.io/download/sl-latest-windows-x64.zip' -OutFile $(Agent.HomeDirectory)\sl.zip
Expand-Archive -Path $(Agent.HomeDirectory)\sl.zip -DestinationPath $(Agent.HomeDirectory) -Force\
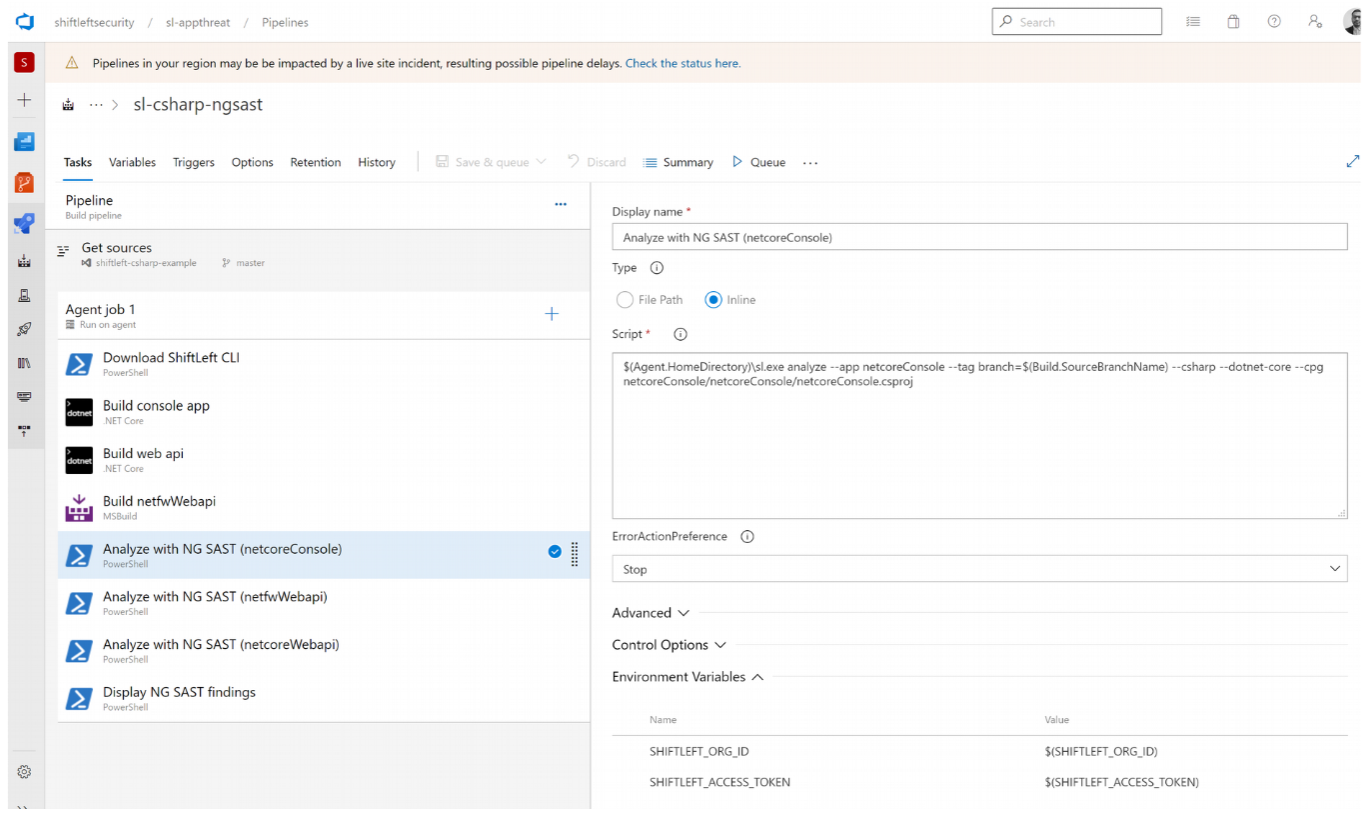
Step 2: Run preZero
Next, create another inline task to run Qwiet and analyze your code. The required script is:
$(Agent.HomeDirectory)\sl.exe analyze --app netcoreConsole --tag branch=$(Build.SourceBranchName) --csharp --dotnet netcoreConsole/netcoreConsole/netcoreConsole.csproj
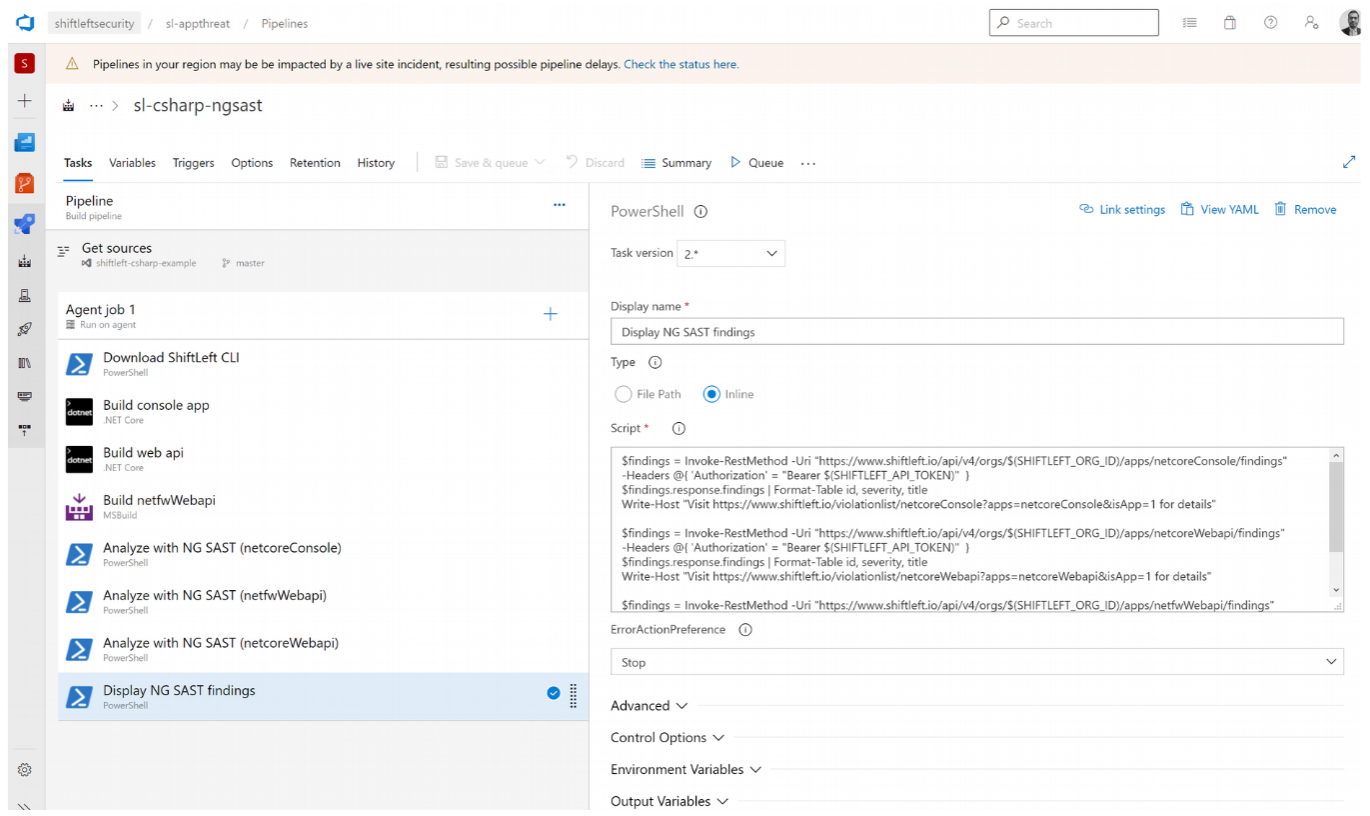
Step 3: Display findings
Finally, create your third inline task to display your results:
$findings = Invoke-RestMethod -Uri "https://app.shiftleft.io/api/v4/orgs/$(SHIFTLEFT_ORG_ID)/apps/netcoreConsole/findings" -Headers @{ 'Authorization' = "Bearer $(SHIFTLEFT_ACCESS_TOKEN)" }
$findings.response.findings | Format-Table id, severity, title
Write-Host "Visit https://app.shiftleft.io/findingsSummary/netcoreConsole?apps=netcoreConsole&isApp=1 for details"
Be sure to update the SHIFTLEFT_ACCESS_TOKEN placeholder with your Qwiet access token, which is available in the Qwiet Dashboard under Access Token.
Recursively finding and scanning your solution/project files
The following example shows you how to modify the sl analyze invocation to recursively find all .sln files and scan them with Qwiet:
# Recursively find all .sln files and scan them with Qwiet preZero
# Be sure to change the app.group value from "test-appgroup" to your preferred name
Get-ChildItem -Path . -Filter *.sln -Recurse -ErrorAction SilentlyContinue -Force | ForEach-Object {
sl.exe analyze --csharp --oss-project-dir $($_.Directory) --tag app.group=test-appgroup --app $($_.Name -replace '.sln', '') $($_.FullName)
}
Alternatively, you can recursively find and scan all .csproj files if .sln-based scans are taking too long:
# Recursively find all .csproj files and scan them with Qwiet preZero
# Use this when .sln based scans are taking too long
# Be sure to change the app.group value from ß"test-appgroup" to your preferred name
Get-ChildItem -Path . -Filter *.csproj -Recurse -ErrorAction SilentlyContinue -Force | ForEach-Object {
sl.exe analyze --csharp --oss-project-dir $($_.Directory) --tag app.group=test-appgroup --app $($_.Name -replace '.csproj', '') $($_.FullName)
}
Running sl check-analysis in Azure DevOps
Qwiet's check-analysis feature allows you to compare your analysis results against a set of build rules you've defined. To use check-analysis in your Azure DevOps workflow, you must
first enable build validation on your branch.