Source Code View
For each application whose code is analyzed and results are tracked by ShiftLeft, the Dashboard allows you to view the source code location where ShiftLeft identified a vulnerability.
In other words, ShiftLeft can provide URLs that, when used, will direct you to the specific source code lines where the vulnerability occurs.
Background
By default, if you run ShiftLeft from a directory that's also a Git repository, ShiftLeft will automatically attempt to read the URL of the remote contained in the Git metadata. This URL informs the UI regarding hyperlink behavior.
However, if you are:
- Running ShiftLeft from a directory that's not a Git repository
- Using a version control system that does not follow the URL conventions of GitHub, GitLab, or Bitbucket
You can create a custom integration to enable source code linking and viewing.
Configuring the Version Control Integration
You can configure your Version Control Integration using an application's Settings page.
To get to the Settings page, select the Application you want to work with from the Applications View. Then, using the left-hand navigation sidebar, click the Cog icon.
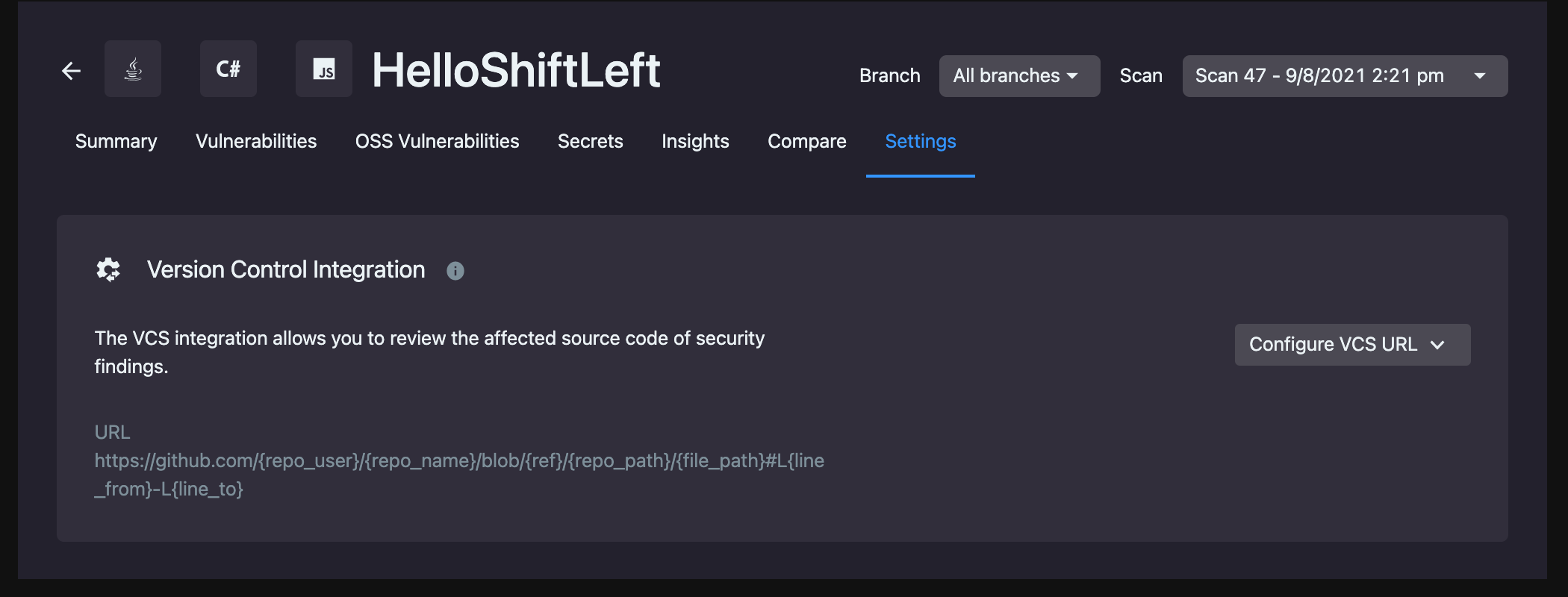
To integrate your version control system with ShiftLeft, provide the URL to your application's source code. ShiftLeft offers a series of templates based on the version control system you use to format the URL correctly.
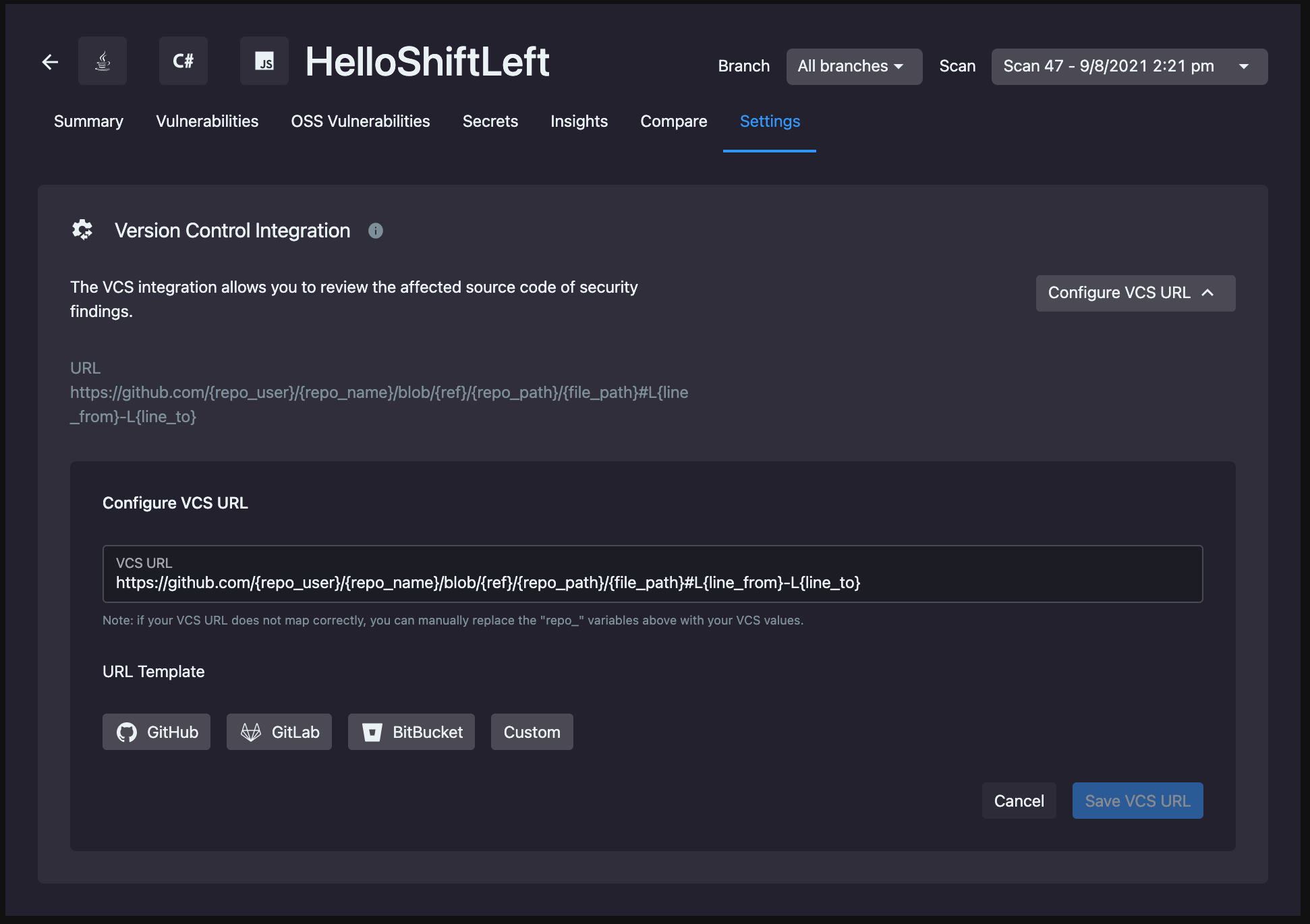
| VCS | Template |
|---|---|
| GitHub | https://github.com/{repo_user}/{repo_name}/blob/{ref}/{repo_path}/{file_path}#L{line_from}-L{line_to} |
| GitLab | https://gitlab.com/{repo_user}/{repo_name}/blob/{ref}/{repo_path}/{file_path}#L{line_from}-L{line_to} |
| Bitbucket | https://bitbucket.org/{repo_user}/{repo_name}/{repo_path}/{file_path}#lines-{line_from},{line_to} |
| Custom | https://{repo_host}/{repo_user}/{repo_name}/{repo_path}/{file_path}/{file_path}#L{line_from}-L{line_to} |
Notes:
- You can append
_escapedto any of these placeholders (i.e.,{file_path_escaped}), which escapes the values for URL queries. - You can use
{commit_or_ref}instead of{ref}. If so, the placeholder will be replaced with the commit hash if available (otherwise, it will be replaced with ref). However, note that some version control systems may not accept this value since the commit hash may correspond only to a local copy.
Once you've provided the URL to your source code, click Save VCS URL.
You can change the URL or see the templates again at any time by clicking Edit URL after the initial configuration.
At this point, your Data Flow information contains active hyperlinks that will lead you to where the identified vulnerability is in the source code.
Modifying the Source Code Filepaths Used
If your repo's file structure doesn't match the predefined templates NG SAST uses, you can provide modifications when running sl analyze.
The --vcs-prefix-correction flag allows you to append information to create the correct filepaths for your code:
sl analyze <parameters omitted> --vcs-prefix-correction "prefixToMatch=prefixToAdd"
Example Usage
If you include the following flag when running sl analyze...:
--vcs-prefix-correction "/io/shiftleft=/path/prefix/to"
NG SAST will find all instances of /io/shiftleft and prepend /path/prefix/to to form /path/prefix/to/io/shiftleft.
For Azure Users
When setting up VCS in the dashboard, select a Custom URL template and use the following:
Be sure to replace <YOUR_AZURE_ORG>, <YOUR_PROJECT_NAME>, and <YOUR_REPO_NAME> with your values.
Usage Notes
The * is a special case that means "prefix all" and will be applied along with any other prefixes you supply; it is not a wildcard. So, if you use *=/src/main, NG SAST will add /src/main to the start of all your file paths.
You can include as many --vcs-prefix-correction flags as necessary, but each prefix is mutually exclusive (the exception is if you use *). So, if you run:
sl analyze ... --vcs-prefix-correction "*=/src/main" --vcs-prefix-correction "/io/shiftleft=/path/prefix/to"
Then NG SAST converts:
/com/shiftleft/utilsinto/src/main/com/shiftleft/utils/io/shiftleft/stream/utilsinto/src/main/path/prefix/to/io/shiftleft/stream/utils
Inferences
NG SAST may infer version control information and provide links based on information obtained from the running containers' environment variables.
For example, if the GITHUB_RUN_ID is present, NG SAST assumes that you're running NG SAST against a GitHub repo via GitHub Actions. Alternatively, if you're running NG SAST using Jenkins, the GIT_URL or GITHUB_REPO_GIT_URL plus BRANCH_NAME, GIT_LOCAL_BRANCH, or GIT_BRANCH provides branch-related information.
However, NG SAST supports your use of the following environment variables; if you set any of these, they will be used instead of the value that NG SAST inferred from your run environment.
SL_VCS_TEMPLATESL_VCS_REPO_NAMESL_VCS_USER_NAMESL_VCS_COMMIT_IDSL_VCS_BRANCH_REFSL_VCS_RELATIVE_PATHSL_VCS_ORIGIN_URL